While we had been performing penetration testing to our client, we found a vulnerability in one of our client’s third-party services. Now, we have already reported this vulnerability to our client and also to Mitre Corporation for the publication for CVE-2019-11013 with our client’s consent.
We found a vulnerability in the service named “Nimble Streamer” Nimble Streamer is a service that provides a video streaming function. Nimble Streamer version from 3.0.2-2 to 3.5.4-9 are affected by this vulnerability. However, this vulnerability is now fixed on the latest version, any users who are not using the most recent release, please consider doing an update to the newest version.
The vulnerability that we found is called “Path traversal” sometimes it is called “Directory traversal.” This vulnerability allows any users to access files on a server that the server is not intended to. This vulnerability is occasionally caused by the server intentionally allowing using URL that references an object on the server directly to access any some contents on the server such as a video file to display it on a webpage. By changing any URL that is legitimately referencing any file on the server to any other data on the server resulting in the server also use that file to show on the webpage.
This is an example webpage that we found a vulnerability. It allows users to provide a URL of a video to test the streaming on this webpage.
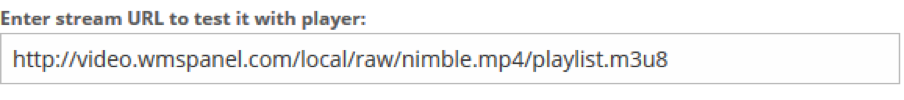
We can see that URL is already in the input field, which is a URL of an example video, being referencing a video file on the server which is “nimble.mp4”.
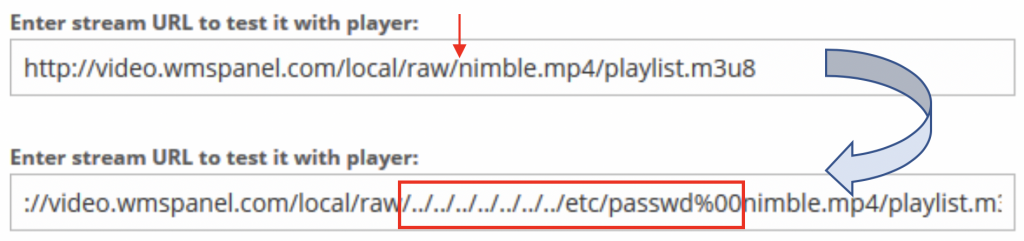
We will test this vulnerability by changing the URL a common readable file that might be on the server such as “/etc/passwd.” We will insert some set of “../” (dot dot slash) before the word “nimble.mp4” following by “/etc/passwd” and “%00” which is a special character that is used to define that “at this point is the end of the string”, then we will have a URL look like this.
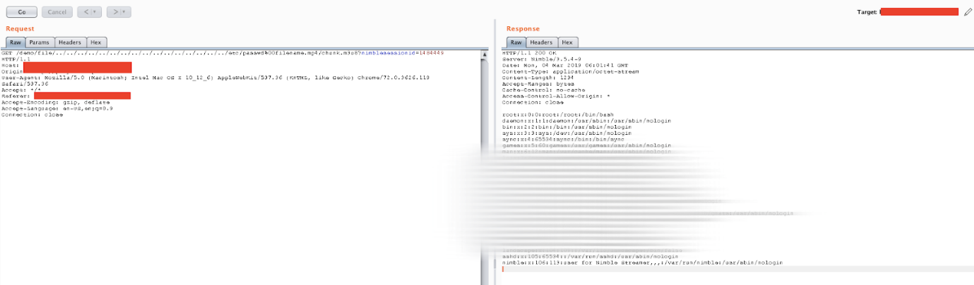
Next, we will send this URL to the server by using Burp Suite to help analyze the results, and the result is the server returns the content of file “/etc/passwd” as we expected.
To prevent the path traversal vulnerability, We recommend the developer to consider more about these tactics to use while implementing any application. First, an input validation, by validate input against a whitelist and reject other input that does not match the list. Importantly do not accept the file and path separator if necessary. Second, using cryptographically secure random strings to map the resources on the server instead of allowing using direct URL to access them. Lastly, limiting the privilege of the account that operates the server to be as less as necessary to narrow the damage that might cause if any vulnerability occurred.
Timeline
2019-03-03 – Vulnerability was found by MAYASEVEN
2019-03-04 – Research team report the issue to Nimble Streamer Developer and Support
2019-03-13 – The vulnerability was fixed in version 3.5.5-1
2019-03-21 – Request to publish the vulnerability
2019-08-18 – Published a blog about POC